38 Solved Questions with Answers
-
2025
Terrorism is a global scourge. How has it manifested in India? Elaborate with contemporary examples. What are the counter measures adopted by the State? Explain. (150 words)
Approach:
- Introduction: Define terrorism, its global significance, and its impact on international peace, stability, and human security.
- Body: Discuss Manifestation of Terrorism in India, Give Contemporary Examples of Terrorism in India, highlight the effectiveness of India’s countermeasures.
- Conclusion: Emphasize the need for continuous adaptation to new threats.
Under the Bharatiya Nyaya Samhita, "terrorism" is defined as any act committed with the intention to threaten the unity, integrity, and security of India, intimidate the public or a segment thereof, or disturb public order. Globally, it threatens peace, development, and human security, with organizations like ISIS, Al-Qaeda, and Boko Haram spreading fear, destabilizing states, and disrupting international trade and governance.
Manifestation of Terrorism in India
1. Cross-Border Terrorism: Pakistan-based groups like Lashkar-e-Taiba (LeT) and Jaish-e-Mohammed (JeM) are behind major attacks in India.
- Examples include the 2008 Mumbai attacks and the 2019 Pulwama attack and 2025 Pahalgam terror attack, causing extensive loss of life and destabilization.
2. Radicalization and Homegrown Terrorism: Radicalization, often through social media, has led to lone-wolf attacks and recruitment for terrorist organizations.
- Recent examples include ISIS-inspired groups and attacks like Pathankot (2016).
3. Religious Terrorism: Radicalized religious groups engage in violence, citing religious motivations for attacks on minorities or state authorities.
- The 2016 Bengaluru bombing and Kashmir militancy have been manifestations of this.
4. Northeastern Insurgencies: ULFA, NSCN-K, and other groups demand autonomy or secession from India.
- Their activities destabilize the Northeast, with violent attacks on civilians and security forces.
5. Left-Wing Extremism (LWE): Maoist insurgents (CPI-Maoist) in Chhattisgarh, Jharkhand, and Orissa engage in violence, targeting security forces and government infrastructure.
- These groups aim to overthrow the government through armed rebellion, causing widespread disruption and casualties.
6. Cyberterrorism: Terrorist groups use cyberspace to launch cyberattacks on critical infrastructure, spread propaganda, steal sensitive data, and recruit members online.
- Example: In May 2025, Jasim Shahnawaz Ansari was arrested for over 50 cyberattacks on Indian government websites, using Distributed Denial of Service(DDoS) tools to disrupt services during Operation Sindoor.
7. Sectarian Violence: Tensions between Hindu-Muslim communities sometimes lead to violence, such as riots and targeted attacks.
- Though not all are classified as terrorism, they often have similar ideological motivations.
Contemporary Examples of Terrorism in India
1. 2025 Pahalgam Terror Attack: On 22 April 2025, The Resistance Front (TRF) militants, a proxy of LeT, opened fire on tourists at Baisaran Valley, Pahalgam, killing 26 civilians and injuring around 20. Victims were targeted based on religious identity. It is the deadliest civilian attack in India since the 2008 Mumbai attacks.
2. Maoist Attacks in Chhattisgarh: In 2021, Maoists ambushed a police convoy, killing several officers in Chhattisgarh.
- Left-wing extremism continues to challenge India’s internal security, especially in the Red Corridor.
3. 2019 Pulwama Attack: A suicide bomber from JeM killed 40 CRPF personnel in Jammu & Kashmir.
- This attack led to a major escalation between India and Pakistan, including India’s airstrike on Balakot.
4. 2016 Pathankot Attack: JeM militants attacked the Pathankot Air Force Station, killing 7 security personnel.
- This highlighted vulnerabilities in India’s defense infrastructure and its porous border with Pakistan.
5. 2008 Mumbai Attacks: LeT militants launched a series of attacks in Mumbai, killing 166 people and injuring hundreds.
- This highlighted the vulnerability of urban infrastructure to well-coordinated terrorist attacks.
6. Radicalization and ISIS Modules: Various ISIS-inspired terrorist modules have been detected in Kerala, Tamil Nadu, and Kashmir, recruiting young individuals for terrorism.
- These radicalized youths are often influenced by online content and external terror organizations.
Countermeasures Adopted by the State
1. Legislative Measures: UAPA (1967) and the NIA Act (2008) empower Indian authorities to investigate, detain, and prosecute terrorists.
- The Unlawful Activities (Prevention) Act (UAPA) allows preventive detention, seizure of property, and outlawing of terrorist organizations.
2. National Investigation Agency (NIA): The NIA is tasked with investigating and prosecuting terror-related crimes, ensuring a unified national response.
- The agency has taken action in cases like Pathankot, Pahalgam and Pulwama.
3. Security Operations: Indian Army and National Security Guard (NSG) conduct regular counter-terror operations to neutralize militant groups.
- Operation All Out in Kashmir and anti-Naxal operations in Chhattisgarh are ongoing measures.
4. Border Security Enhancement: BSF and ITBP bolster security at India’s borders with Pakistan, Bangladesh, and Myanmar to prevent cross-border terrorism.
- Surveillance systems, drone patrolling, and border fencing are critical to reducing infiltration.
5. Intelligence Sharing and Technology: Agencies like the Intelligence Bureau (IB), R&AW, and NTRO share intelligence to preempt terrorist activities.
- Technologies like AI, drones, and biometrics aid in surveillance and threat detection.
6. Counter-Radicalization Programs: Community-based de-radicalization programs are in place, particularly in Kashmir, to engage with youth and prevent radicalization.
- The Jammu & Kashmir Police have implemented rehabilitation programs for surrendered militants.
7. International Cooperation: India has worked with global agencies like Interpol, FBI, and UNODC to combat transnational terrorism.
- India has consistently pushed for an international convention on terrorism at the UN.
8. Public Awareness Campaigns: Cyber surveillance and counter-narrative campaigns focus on curbing extremist ideologies, especially in vulnerable youth groups.
- India has implemented initiatives such as the National Counter Terrorism Centre (NCTC) to coordinate and share anti-terror strategies across states.
The state has developed a multi-faceted approach to combat terrorism. Yet, the evolving nature of terror threats calls for constant innovation—leveraging AI-driven surveillance, robust cybersecurity, deradicalization initiatives, regional intelligence cooperation, and socio-economic development in vulnerable regions. A balanced approach that combines hard security measures with preventive strategies will be key to safeguarding national security while addressing the root causes of radicalization. However, the evolving nature of terrorism demands continuous adaptation in strategies, improved international collaboration, and the adoption of modern technologies to safeguard national security and prevent further radicalization.
-
2025
The Government of India recently stated that Left Wing Extremism (LWE) will be eliminated by 2026. What do you understand by LWE and how are the people affected by it? What measures have been taken by the government to eliminate LWE? (Answer in 150 words)
Approach
- Introduction: Define Left-Wing Extremism (LWE) and mention briefly their origin.
- Body: Discuss the impact of LWE on people, explain the government measures to eliminate LWE and briefly mention the success and progress made.
- Conclusion: Summarise by emphasising the effectiveness of India’s SAMADHAN doctrine, and the need for continued governance and inclusive development.
Introduction
Left-Wing Extremism (LWE), also known as Naxalism, is an armed insurgency led by Maoist groups aiming to overthrow the government through violence. It originated from the Naxalbari movement in 1967 (West Bengal) and has spread across various parts of India, particularly within the Red Corridor.
Impact of LWE on People
- Disrupt essential services such as education, healthcare, connectivity, and banking.
- Isolate communities from development.
- Violence destroys infrastructure—roads, schools, hospitals—and leads to significant loss of life.
- Young people are often coerced into joining insurgency groups, leaving families and communities in distress.
- The constant presence of armed insurgents creates fear, insecurity, and trauma among residents.
- Example: Salwa Judum is a group of tribal persons mobilized for resistance against outlawed armed naxalites. It was argued that the displaced individuals, residing in forest areas across several states, have been deprived of essential welfare schemes, including land rights, tribal status, social welfare benefits, and Forest Rights Act entitlements.
Government Measures to Eliminate LWE
- National Policy and Action Plan (2015): Modernized security forces, strengthened intelligence, and enhanced operational capabilities of central and state police.
- Zero-tolerance Policy: Through schemes like the Security-related Expenditure (SRE), the government reimburses costs incurred by states for security operations, training, and other expenses.
- Infrastructure Development and Connectivity: 3 telecom projects are being implemented (including 4G connectivity). The construction of Fortified Police Stations (FPSs) has increased significantly, from 66 in 2014 to 612 in 2024.
- Social and Economic Empowerment: New bank branches, ATMs, 48 ITIs, 61 Skill Development Centers, and 178 Eklavya Model Residential Schools. The Dharti Aaba Janjatiya Gram Utkarsh Abhiyan (2024) benefits 1.5 crore people in 15,000 villages.
- Civic Engagement and Awareness Programs: Programs like Civic Action Program (CAP), media campaigns, and Tribal Youth Exchange Programs build trust and counter Maoist propaganda.
- SAMADHAN doctrine: A one-stop solution for the LWE problem. It encompasses the entire strategy of government from short-term policy to long-term policy formulated at different levels. SAMADHAN stand for: Smart leadership, Aggressive strategy, Motivation and training, Actionable intelligence, Dashboard-based KRAs, Harnessing technology, Theatre-specific action plans, No access to financing
Success and Progress
Violent incidents dropped by 81% (1,936 in 2010 to 374 in 2024), and deaths fell by 85%. LWE-affected districts reduced from 126 in 2018 to 38 in 2024. Thousands of Naxals have surrendered, been arrested, or neutralized—290 neutralized, 1,090 arrested, and 881 surrendered in 2024 alone.
Conclusion
LWE is both a security and socio-economic challenge rooted in alienation. Its elimination requires a balance of strong security and inclusive development, reflecting the triumph of democracy’s promise of justice and equity.
-
2025
What are the major challenges to internal security and peace process in the North-Eastern States? Map the various peace accords and agreements initiated by the government in the past decade. (Answer in 250 words)
Approach:
- Introduction: Write about the North-Eastern region state included in it.
- Body: Mention the major internal security challenges faced by the region and recent initiatives to maintain peace in the region.
- Conclusion: Conclude with a way forward approach for everlasting peace in the region.
Introduction:
The North-Eastern region of India, consisting of eight states (the Seven Sister States and Sikkim), is marked by its distinct geographical and cultural identity. Sharing borders with China, Nepal, Bhutan, Bangladesh, and Myanmar, this region holds strategic significance. However, the region has been subjected to several internal security challenges, the latest among them is violence between the Meitei and Kuki-Zo communities. Since May 2023, Manipur has witnessed violent clashes between the Meitei and Kuki-Zo communities, leading to over 250 deaths and the displacement of more than 60,000 people, fueled by ethnic, land, and political tensions.
Body:
Major Challenges to Internal Security and Peace
- Ethnic Conflicts: Manipur has witnessed severe ethnic violence, particularly between the Meitei and Kuki communities, leading to over 250 deaths and the displacement of more than 60,000 people since May 2023.
- Insurgency and Armed Groups: Despite several peace accords, insurgent factions like the United Liberation Front of Asom (ULFA) continue to pose challenges to regional stability.
- Inter-State Border Disputes: Territorial conflicts, such as those between Assam and Nagaland, and Assam and Meghalaya, exacerbate tensions and impede peaceful co-existence.
- Rehabilitation and Integration: The reintegration of former militants and displaced populations remains a significant challenge to long-term peace.
- Illegal Migration: Primarily from Bangladesh and Myanmar-has severely disrupted demographics, triggered land encroachments, strained local infrastructure, and fueled ethnic tensions and social unrest.
- Cross-border issues: Insurgents use safe havens in Myanmar and illicit arms/drug trade through the “Golden Triangle.”
- Infrastructure & governance deficits
Recent Peace Accords and Initiatives (2015–2025)
- Naga Peace Accord (2015): Aimed at resolving the Naga insurgency through a framework agreement with National Socialist Council of Nagaland (NSCN)
- Bodo Peace Accord (2020): Resulted in the creation of the Bodoland Territorial Region (BTR) with enhanced autonomy.
- Bru-Reang Agreement (2020): Facilitated the permanent settlement of Bru refugees in Tripura.
- Karbi Anglong Agreement (2021): Led to the surrender of over 1,000 militants and the establishment of the Karbi Anglong Autonomous Territorial Council.
- Adivasi Peace Accord (2022): Addressed the issues of Adivasi communities in Assam, leading to militant surrender and autonomy formation.
- Dimasa National Liberation Army (DNLA) Agreement (2023): The peace accord between Indian government, Assam government, and the DNLA (Dimasa People's Supreme Council) agreed to end the insurgency in Dima Hasao district, with over 168–181 cadres surrendering arms and disbanding the outfit.
- Manipur Peace Agreement (2023): Aimed at ending insurgency through a peace accord with the United National Liberation Front (UNLF). It brought an essential breakthrough in Manipur’s peace process by ending decades of hostilities and signaling the return of militant actors to the democratic mainstream,
- Tripura Peace Accord (2024): Signed between the Government of India, Tripura, and insurgent groups NLFT and ATTF, it ended a 34-year insurgency with 328 cadres surrendering. The accord included a Rs. 250-crore rehabilitation and tribal development package to ensure lasting peace and stability.
Conclusion
While significant strides have been made in fostering peace through accords, challenges such as ethnic conflicts, border disputes, and rehabilitation efforts persist. Sustaining peace in the Northeast requires inclusive development, effective border management, and rehabilitation of former militants alongside strong governance reforms. The Centre’s “North East Vision 2035”, with focus on connectivity, digital inclusion, and sustainable growth, coupled with recent peace accords, provides a roadmap to transform the region into a hub of stability, prosperity, and strategic strength.
-
2025
Why is maritime security vital to protect India's sea trade? Discuss maritime and coastal security challenges and the way forward. (250 words)
Approach:
- Introduction: Define maritime security and its importance to India's sea trade and national interests.
- Body: Explain its importance for trade, energy, and regional influence; identify key challenges including geopolitical tensions, institutional gaps, and operational threats; suggest reforms in surveillance, coordination, and international cooperation.
- Conclusion: Reaffirm the role of maritime security in protecting India’s trade and ensuring regional leadership.
Answer: Maritime security refers to the protection of a nation’s maritime interests, including sea trade routes, coastal regions, and port infrastructure, from threats like piracy, terrorism, and trafficking. For India, with a 7,500 km coastline and 90% of trade by volume via the sea, it is an economic and strategic lifeline. Ensuring maritime security is essential for energy access, regional leadership, and national resilience.
Significance of Maritime Security for India’s Sea Trade
1. Trade Backbone: Over 90% of India’s international trade by volume is sea-borne, making port and route security vital.
2. Energy Access: ~85% of crude oil imports arrive via vulnerable sea lanes like the Strait of Hormuz and Strait of Malacca.
3. Strategic Location: India’s central position in the Indian Ocean Region (IOR) allows control over major east–west trade routes.
4. Blue Economy Growth: Marine sectors contribute ~$137 billion to GDP and support ~4 million coastal livelihoods.
5. Seafood Exports: India is a major seafood exporter; security disruptions impact revenue and food chains.
6. Port Infrastructure Expansion: Major projects under Sagarmala demand heightened security for economic viability.
7. Digital Port Logistics: Increasing digitization of ports poses new cyber-security vulnerabilities.
8. Island Territories: Andaman and Nicobar Islands are key for forward maritime surveillance.
9. FDI Attraction: Secure sea trade zones attract foreign direct investment and improve Ease of Doing Business.
10. Geopolitical Influence: Security enhances India’s credibility in regional forums like QUAD and BIMSTEC.
Maritime and Coastal Security Challenges
1. Maritime Terrorism: 26/11 Mumbai attacks exposed critical flaws in coastal patrolling and intelligence sharing.
2. Piracy in IOR: Despite decline, Somali piracy and Southeast Asian maritime crimes continue to threaten commercial shipping.
3. Drug and Arms Trafficking: Coastal routes are exploited for smuggling; e.g., 2023 seizure of heroin off Gujarat coast.
4. Illegal, Unreported, and Unregulated (IUU) Fishing: Foreign trawlers violate India's Exclusive Economic Zone (EEZ), impacting local fishermen and marine organisms and ecosystem as well.
5. China’s Naval Expansion: The "String of Pearls" strategy includes bases in Gwadar, Djibouti, and Hambantota, encircling India.
6. Jurisdictional Overlaps: Lack of coordination among Navy, Coast Guard, and marine police reduces response efficiency.
7. Outdated Coastal Infrastructure: Many minor ports and fisheries lack surveillance and physical barriers.
8. Cyber Threats to Port Systems: Increasing digital interfaces in shipping logistics are prone to hacking and ransomware.
9. Limited Capacity of Coastal Police: Poor training, shortage of boats, and limited sea-faring skills hinder security.
10. Natural Disasters: Cyclones, tsunamis, and rising sea levels threaten coastal installations and naval bases.
Way Forward for Strengthening Maritime Security
1. National Maritime Authority: Establish a single-point command to coordinate Navy, Coast Guard, and other agencies.
2. Expansion of Coastal Radar Chain: Install radar stations across all coastal states and islands for real-time vessel tracking.
3. Automatic Identification System (AIS) Mandate: Enforce AIS on all fishing and merchant vessels to avoid unidentified entries.
4. National Command Control Communication and Intelligence (NC3I) Network: Ensure data fusion and surveillance across all coastal stakeholders.
5. SAGAR (Security and Growth for All in the Region): Strengthen regional maritime partnerships and naval diplomacy.
6. Indian Ocean Naval Symposium (IONS): Use IONS to share intelligence and conduct joint patrols in IOR.
7. Port Modernization under Sagarmala: Integrate physical and digital security features in all modern port projects.
8. Coastal Community Engagement: Train local fishermen as "eyes and ears" of the security system under Coastal Security Scheme.
9. Cybersecurity Protocols for Maritime Systems: Regular audits and IT upgrades for port infrastructure.
10. International Cooperation: Collaborate with navies of QUAD (Quadrilateral Security Dialogue) and BIMSTEC for capacity building and joint exercises.
India’s maritime security is central to its economic well-being, energy access, and geopolitical aspirations. The growing complexity of maritime threats requires a multi-pronged approach combining surveillance, institutional reforms, technological integration, and international cooperation. With a forward-looking strategy, India can secure its maritime domain and assert its leadership in the Indo-Pacific.
-
2024
Explain how nacro- terrorism has emerged as a serious threat across the country. Suggest suitable measures to counter narco-terrorism. (Answer in 150 words)
Approach
- Write a brief introduction about Narco-terrorism.
- Explain emergence of narco-terrersm as a threat across the country.
- Mention measures to counter Narco-tererrism.
- Write a holistic conclusion.
Introduction
Narco-terrorism is the use of organized terror by states, insurgents, or criminal networks to achieve political, economic, or social objectives through drug trafficking. Narco-terrorism is increasingly linked to the narcotics-producing regions of the Golden Crescent and the Golden Triangle.
Body
- Narco-terrerism as Threat:
- It creates a dual threat of violence and organized crime, destabilizing nations, corrupting institutions, and fostering insecurity by financing insurgencies, cartels, and extremist networks globally.
- Northeast states of India, Punjab and Jammu & Kashmir are the major Indian states which are suffering with narco-terrerism.
- In India, drug trafficking networks exploit porous borders, particularly with Afghanistan and Myanmar, to finance terrorism.
- Measures to Counter Narco-Terrorism
- Enhanced Border Surveillance: Strengthen border security using advanced technologies like drones, satellite imagery, and AI-based surveillance systems to curb drug smuggling.
- Financial Monitoring: Implement robust financial intelligence mechanisms to trace and disrupt narcotic-linked terrorist funding.
- International Cooperation: Bolster transnational partnerships through organizations like the UNODC and Interpol to dismantle global narco-terror networks.
- Public Awareness and Rehabilitation: Conduct anti-drug awareness campaigns and establish de-addiction programs to weaken the consumer base.
- Legal Reforms: Strengthen laws for stricter punishment against drug traffickers and terror financiers.
Conclusion:
A Multi-faceted approach is essential to counter narco-terrorism. Strengthening border security, enhancing international cooperation, and implementing stringent anti-money laundering measures such as Prevention of Money Laundering Act, 2002 are crucial. Additionally, addressing socio-economic issues, promoting alternative livelihoods, and investing in education can help reduce the appeal of drug trafficking and terrorism, fostering long-term stability.
-
2024
India has a long and troubled border with China and Pakistan fraught with contentious issues. Examine the conflicting issues and security challenges along the border. Also give out the development being undertaken in these areas under the border Area Development Programme (BADP) and Border Infrastructure and Management (BIM) Scheme. (Answer in 250 words)
Approach
- Briefly introduce the historical and geopolitical significance of India’s borders with China and Pakistan.
- Examine the conflicting issues, security challenges along the border, and development initiatives under BADP and BIM.
- Conclude with the significance of combining security measures with development efforts.
Introduction
India’s borders with China and Pakistan are marked by historical disputes and ongoing security challenges.
Body
- India’s Border with China and Pakistan:
- The India-China border, known as the Line of Actual Control (LAC), spans approximately 3,440 km. On the western front, the India-Pakistan border known as Line of Control (LOC) spread about 740 km.
- Conflicting Issues and Security Challenges:
- Chinese Front:
- The primary issue with China is the ill-defined boundary, leading to frequent face-offs and skirmishes. Notable incidents include the Galwan Valley clash, 2020, Doklam military standoff, 2017. The competition to build infrastructure along the LAC further exacerbates tensions.
- Significant smuggling of Chinese electronics and other consumer goods occurs through these India-China border points.
- Pakistan Front:
- The issue with Pakistan is frequent violation of LoC, with cross-border shelling and infiltration attempts by militants. The Pulwama attack of 2019 and subsequent Balakot airstrike are recent examples of the volatile situation.
- Pakistan asserts that the entire Sir Creek, including its eastern bank marked by a "green line" on a 1914 map, belongs to them.
- Chinese Front:
- Border Area Development Programme (BADP):
- BADP aims to develop infrastructure and improve the living conditions of people in border areas.
- Projects include building roads, schools, and healthcare facilities, enhancing both security and socio-economic conditions.
- Developed Karcham-Chitkul Road 40 km road stretch via Sangla in the Kinnaur district of Himachal Pradesh, which shares a border with China.
- Border Infrastructure and Management (BIM) Scheme:
- It helps in the creation of infrastructure such as border fence, border flood lights, technological solutions, border roads and Border OutPosts (BOPs) and company operating bases to secure India's borders with Pakistan, Bangladesh, China, Nepal, Bhutan and Myanmar.
- India plans to build 383 composite border outposts along the India-Bangladesh border, and 126 along the India-Pakistan border.
Conclusion
Through initiatives like BADP and BIM, India is not only enhancing border security but also fostering development in these critical regions, aiming for a balanced approach to border management.
-
2024
Social media and encrypting messaging services pose a serious security challenge. What measures have been adopted at various levels to address the security implications of social media? Also suggest any other remedies to address the problem. (Answer in 250 words)
Approach:
- Introduce the answer by highlighting the proliferation of social media
- Highlight security challenges of social media and encrypted messaging services
- Give current measures to address social media security challenges
- Suggest other remedies to address the problem
- Conclude suitably.
Introduction:
The proliferation of social media and encrypted messaging services has revolutionised communication in India.
- These platforms have become powerful tools for information sharing and connectivity, but they also present complex risks to national security, public safety, and social harmony.
- From the spread of misinformation to facilitating criminal activities, these digital spaces have emerged as a new frontier for security concerns.
Body:
Security Challenges of Social Media and Encrypted Messaging Services:
- Misinformation: Social media spreads false info, fueling unrest. (Manipulated content flooding platforms in 2022 Russia Ukraine War).
- Radicalization: Extremists recruit via encrypted apps. (ISIS on Telegram).
- Cybercrime: Platforms enable scams, identity theft. (2023 deep fake scams with celebrity faces).
- Data Privacy: Misuse of user data raises concerns. (2018 Cambridge Analytica scandal)
- Digital Warfare: Platforms used for disinformation and state interest. (2020 U.S. election manipulation by Russia)
Measures to Address Social Media Security Challenges:
- IT Act 2000: Governs online communication; Section 69A enables blocking content for security, and Section 79(1) grants intermediaries conditional immunity. (India banned 59 Chinese apps in 2020)
- IT Rules 2021: Mandates content moderation and user privacy notifications. (Twitter faced compliance issues in 2021)
- Grievance Officers: Platforms must appoint officers to handle complaints. (Meta appointed Spoorthi Priya in 2022)
- Fact-Checking: Platforms must remove false content flagged by the government. (2023 rule under Supreme Court review)
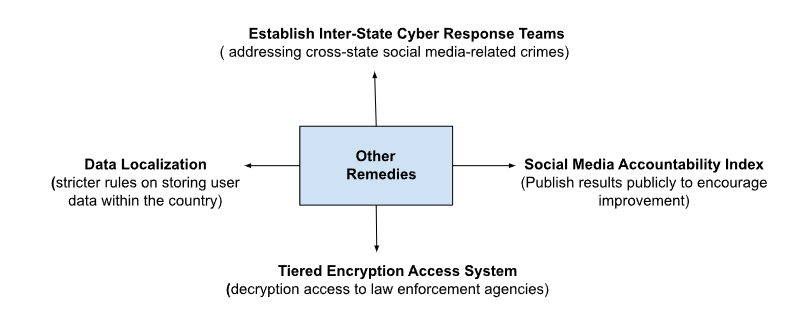
Other Remedies:
Conclusion:
By combining technological solutions, digital literacy initiatives, and collaborative efforts between stakeholders, India can create a more secure online environment. Ultimately, the goal is to strike a delicate balance between national security interests and individual privacy rights, ensuring a safe and vibrant digital ecosystem for all citizens.
-
2023
Winning ‘Hearts and Minds’ in terrorism affected areas is an essential step in restoring the trust of the population. Discuss the measures adopted by the Government in this respect as part of the conflict resolution in Jammu and Kashmir.
Winning of ‘Hearts and Minds’ refers to the government backed people-centric approach to win support of the local people to restore their trust in the system in conflict ridden regions like Kashmir where goal is to counteract the influence of terrorism.
Measures adopted by the government with respect to Kashmir
- Abrogation of Article 370: For greater integration of Jammu and Kashmir with rest of India and bringing youth into mainstream, special status of Jammu & Kashmir has been abrogated.
- Youth participation:
- Under project Sadhbhavana, Army Goodwill Schools (AGS), hostels and vocational courses were launched; teenagers and the elderly were taken on a ‘Bharat Darshan’ and cricket tournaments were organized for youth in the Valley.
- Project Himayat was launched for capacity building and Project Umeed for empowering J&K women.
- Infrastructure Developments: Emphasis has been laid on creating infrastructure in transportation, health etc. For example, PM’s development package for J&K, Khelo India centers in J&K.
- Development of Tourism, Arts and Crafts Sectors: The new Wool Processing, Handicrafts and Handloom Policy, 2020 has been adopted for promotion and development of handicrafts and handloom sector.
- Anti-Radicalisation Drives: To make people of Kashmir feel less alienated and more incorporated towards Indian cause, anti-radicalisation drives were launched.
- Political Engagements: Engagement with young breed of political leaders for encouraging political dialogues and promoting regional youth participation in local politics is being promoted.
Though the government approach is to restore peace, stability, and development in the region, the situation in Kashmir remains complex. It is high time that government implements more such policies for complete integration of the state's people with the rest of India.
-
2023
The use of unmanned aerial vehicles (UAVs) by our adversaries across the borders to ferry arms/ammunitions, drugs, etc., is a serious threat to the internal security. Comment on the measures being taken to tackle this threat.
An Unmanned Aerial Vehicle (UAV) is a “remotely piloted or self-piloted aircraft that can carry cameras, sensors, communications equipment or other payloads like arms/ammunitions, drugs. It can be used by our adversaries across the border and can be a serious threat to internal security.
Cause of concern
- They can fly at high altitudes and low speeds making it difficult for border security forces to detect and intercept them.
- They can be remotely controlled and flown from a safe distance, reducing the risk to human operatives engaging in infiltration attempts.
- Drones can also be used for espionage purposes, allowing unauthorized individuals to gather sensitive information about military installations, critical infrastructure, and other key targets.
Measures taken by Indian government to tackle threats
- Technological Upgradation: Deployment of anti-drone weapons, detection systems like radars, jammers, e.g., anti-drone systems like the SkyWall 100 and the DroneGun Tactical CHIMERA anti-drone system, developed using French technology.
- Military Intelligence: The BSF conducts round-the-clock surveillance through patrolling, checkpoints, and observation posts, erected a border fence and installed floodlights.
- Institutional: MHA has established Anti Rogue Drone Technology Committee (ARDTC) to evaluate the technology available to counter rogue drones.
- Governmental Collaboration: Active collaboration with countries like Israel for high end drones.
- DRDO Nishant: Primarily designed for intelligence-gathering over enemy territory, it is also used for reconnaissance, training, surveillance, target designation, artillery fire correction, and damage assessment.
- Counter-Unmanned Aircraft Systems (C-UAS) strategy: It includes blocking communication lines and bringing down unwanted drones.
With the emergence of technology comes the threat to internal security. Therefore, a comprehensive drone strategy that includes private participation for developing high end drones is the need of an hour.
-
2023
What are the internal security challenges being faced by India? Give out the role of Central Intelligence and Investigative Agencies tasked to counter such threats.
A sovereign nation's foremost responsibility is the safety of its citizens from external as well as internal challenges. Since independence, India has tackled various internal security challenges including insurgency, militancy and externally induced rebellions.
Internal security challenges for India
- Separatist Movements: Separatist feelings have been present ever since the birth of our nation and still continue to be a cause of misery for law and order. For example, Nagaland separatism, Kashmiri separatism etc.
- Communalism: The contentions between the two major religious groups have often led to brewing of hatred and fights. This further fuels separatist tendencies. Hate among groups makes our citizens easy targets to be motivated for terrorist activities.
- Illegal Migration: Over the years, illegal migration has led to a lot of associated problems such as demographic change and increased unemployment thereby straining the nation’s resources.
- Left-Wing Extremism: It is noticed in the central and eastern parts of India and is marked by Marxism or Maoism as its political ideology. Socio-economic disparities and land alienation are the factors responsible for its emergence.
Various intelligence and investigative agencies work in India with different mandates of performing actions.
- National Investigation Agency (NIA): It is the premier counter-terrorism law enforcement agency of India, investigating offences that affect the sovereignty, security and integrity of India.
- Narcotics Control Bureau (NCB): It is the apex body to coordinate between various narcotics and drug law enforcement agencies. It works to prevent drug trafficking across India.
- Directorate of Revenue Intelligence (DRI): This is the body dealing with intelligence of smuggling of contrabands and investigating cases related to it. It also looks to prevent proliferation of black money and money laundering.
- Intelligence Bureau (IB): It is the apex intelligence body responsible for collecting information within the country and executing counter-terrorism operations. It deals with matters of domestic intelligence and internal security.
- Research and Analysis Wing (R&AW): It took the operations of handling foreign intelligence from Intelligence Bureau. It now collects foreign intelligence, conducts counter-terrorism operations and advises Indian policymakers.
- Central Bureau of Investigation (CBI): It is the premier investigating police agency made on the recommendation of the Santhanam Committee. It carries out investigation and also acts as the point of access for the Interpol.
Internal security is imperative for the growth of a nation. Indian Intelligence and Investigative Agencies are the unsung heroes of our nation and have done a great deal in securing our lives.
-
2023
Give out the major sources of terror funding in India and the efforts being made to curtail these sources. In the light of this, also discuss the aim and objective of the No Money for Terror (NMFT) Conference recently held at New Delhi in November 2022.
Ever since its birth in 1947, India has been a witness to various kinds of terrorist and insurgent activities. Over the years India has learned from its mistake and evolved numerous ways to tackle terror funding and other related activities.
Major sources of terror funding
- State Sponsorship: The use of terror to further diplomatic interests is a known practice. States sponsor crimes and support terrorist to be able to use them when needed for their purpose.
- Counterfeit Currency: It involves directly printing and circulating fake currency in the market. Alternatively, this is a tool used by neighbouring states to destabilize the Indian economy.
- Organised Crime: Criminal organizations generally work in nexus and are often connected to bigger terrorist groups. The flow of resources is two-ways between these two.
- Extortion: This remains the biggest source of funding of terrorism in India especially in the North-East.
- Hawala System: This is an illegal method of transferring money, generally through international borders that is used by criminal networks.
Efforts to curtail sources
- National Investigation Agency (NIA): It is the premier agency in India for combating terror across states without special permission from the states.
- Unlawful Activities Prevention Act: This anti-terror legislation seeks to designate an individual as a “terrorist”.
- National Intelligence Grid (NATGRID): It is a centralised data library of terror and crime related information.
- SAMADHAN Doctrine: Developed specifically for the Left-Wing Extremism problems, it also aims to curb the access of terror organizations to funds.
Recently, the third No Money for Terror (NMFT) Ministerial Conference on Counter-Terrorism Financing was held in New Delhi, India. It sought to:
- Collaborate with countries around the world to curtail terror and extremist funding.
- To set up a secretariat regarding the same in the country, which won't be an investigative body but operate on the concept of collaboration and cooperation.
- To investigate new and emerging threats and methods of propagating terrorism.
Being surrounded by two hostile neighbours does not allow India any leeway for complacent behaviour on the question of internal security. Through several measures, India continues to fight the battle against terrorism.
-
2022
Discuss the types of organised crimes. Describe the linkages between terrorists and organised crime that exist at the national and transnational levels.
Illegal activities carried out at a large scale for profit through organisation and planning by powerful criminal groups are known as organised crime.
Some major types of organised crime are smuggling, racketeering, drug and human trafficking, etc.
Organised crime can be broadly categorised as ‘traditional’ and ‘non-traditional’. The former includes activities such as extortion, contract killings, smuggling, etc., while the latter includes cybercrime, enterprise and political corruption, white collar crimes, etc.
Terrorism is not classified as an organised crime since it is driven by a political and ideological agenda and not profit-making. Nevertheless, both organised crime and terrorism often complement each other.
Terrorists primarily require two things for carrying out their activities — financing and logistical support, often provided by entities engaged in organised crime. Sometimes, even terrorists carry out activities that fall under the purview of organised crime. For example, extortion by Left Wing Extremists for financing their activities against the state.
Further, as showcased by the 1993 bombings in Mumbai, entities and individuals in organised crime also provide logistical support to terrorists such as smuggling of dangerous material(s), providing human resources, communication network(s) and information, arranging financial help etc.
Thus, organised crime and terrorism share close linkages at both national and transnational levels and pose a significant threat to the security of the country.
-
2022
What are the maritime security challenges in India? Discuss the organisational, technical and procedural initiatives taken to improve the maritime security.
India has more than 7000 km long maritime border shared with seven nations. Instruments of maritime security protects the territorial sovereignty of nation from possible marine threats.
Challenges-
- Issues of smuggling and human trafficking across the marine border.
- Issues of cross border terrorism.
- Infiltration of illegal migration.
- Issues of piracy in maritime trade.
- Maritime environmental hazards.
- Some Initiatives taken by India-
Organisational-
- India launched security and growth for all (SAGAR) policy to integrated collaboration with Indian ocean region nations.
- India introduced the establishment of integrated theatre command.
- India set up an International fusion centre (IFC) for Indian ocean region in Gurugram.
- Recently quad launched Indo-pacific partnership for maritime domain awareness (IPMDA) for better coordination and awareness.
- India is part of various organisations and dialogue like IONS, IORA and India- EU maritime dialogue.
Technical-
- Mission based deployment of naval ships and aircrafts. Like, INS Vikrant, Nuclear Submarines and project 75I etc.
- India is working on digital cargo and bay arrangement optimization to enhance efficiency of maritime security.
- India introduced advanced Electronic Warfare System ‘Shakti’ in Indian Navy.
- India used advance electronic and digital surveillance over the marine border.
Procedural-
- Being signatory of United Nations Convention on the Law of the Sea (UNCLOS), India adheres all its rules and regulations.
- India follows the procedure of operational interactions with friendly nations via joint exclusive economic zones (EEZ) surveillance.
Way forward
- Swift coordination and collaboration of various security institution is much needed. It can enhance the efficiency in maritime security services.
- Multilateral information sharing is key to prevent marine threats. So, there should be an integrated multilateral data sharing platform.
- Best practices of other marine nations should be shared among all friendly nations holistically.
-
2022
What are the different elements of cyber security? Keeping in view the challenges in cyber security, examine the extent to which India has successfully developed a comprehensive National Cyber Security Strategy.
Cyber security means the protection of cyberspace including critical information infrastructure from attacks, damage, misuse and economic espionage. It also includes the set of technologies and practices designed to prevent various types of cybercrimes.
There are certain key elements of cyber security such as:
- Application Security: It includes measures that are taken during an application’s development process to protect it from threats emerging from flaws in the app design, development, deployment, etc.
- Information security: It is related to protecting information from unauthorized access to avoid identity theft and protect privacy.
- Network Security: It includes activities to protect the network's usability, reliability, integrity and safety.
- Disaster Recovery Planning: It is a process that includes performing risk assessment, establishing priorities and developing recovery strategies in case of a cyber-attack.
- End-user awareness: This includes the dissemination of information and raising awareness about the various facets of cybersecurity among the larger public
Challenges related to cyber security are centred around certain key issues such as:
- An increase in cyber-attacks on critical infrastructure has been witnessed in recent times.
- The lack of adequate necessary infrastructure and human resources trained in dealing with cybersecurity-related issues.
- Inadequate focus on cyber security by the private sector on developing preparedness for dealing with cyber-attacks.
- The country's expanding digital ecosystem and inadequate infrastructure and procedures render large amounts of data vulnerable to cyber-attacks.
- Further, India is not a signatory to the Budapest Convention which seeks to address cybercrimes by improving investigative techniques and increasing cooperation among nations.
India has adopted a multi-faceted National Cyber Security Strategy to deal with cybercrime.
- The Information Technology Act, passed in 2000 and amended in 2008, deals with the mitigation of cybercrime and related issues.
- The constitution of specialised agencies dealing with cybercrime such as the Indian Computer Emergency Response Team (CERT-In), National Critical Information Infrastructure Protection Centre (NCIIPC) and Indian Cyber Crime Coordination Centre (I4C).
- Other government initiatives related to spreading awareness about and mitigating cybercrime-related threats are the Cyber Surakshit Bharat Initiative, National Cyber Security Coordination Centre (NCCC), Cyber Swachhta Kendra and Information Security Education and Awareness Project (ISEA).
- A National Cyber Security Policy was implemented by the government in 2013 for dealing with cybercrimes.
- Further, in 2020, the National Cyber Security Strategy was conceptualised by the Data Security Council of India (DSCI) headed by Lt General Rajesh Pant. This is yet to be implemented by the Centre.
Thus, with the changing nature of cybercrimes, India has also made efforts at meeting the challenges emanating from them. However, more needs to be done to effectively address the threats posed by cybercrimes.
-
2022
Naxalism is a social, economic and developmental issue manifesting as a violent internal security threat. In this context, discuss the emerging issues and suggest a multilayered strategy to tackle the menace of Naxalism.
Naxalism is considered as the biggest security threat to the country. The term Naxalism derives its name from the village Naxalbari of West Bengal. The Naxal Movement started in 1967 under the leadership of Kanu Sanyal and Jagan Santhal as a rebellion against the local landlords over a land dispute. The movement was spread across the eastern Indian and in less developed states like Odisha, Chhattisgarh, and Andhra Pradesh.
Emerging Issues
- The Forest (Conservation) Act, 1980 deprives tribal to depend upon forests produces and there is a massive displacement of tribal population due to developmental and mining projects.
- The administration fails to provide essential services to the people of Naxalite affected regions such as education, freedom, sanitation, and food. There is a confusion over tackling Naxalism as a social issue or as a security threat.
- Some villages suffer with infrastructural problems such as communication and connectivity. There is absence of technical intelligence to fight with Naxalites.
- Lack of political participation by the tribal community and the inability of political authority to provide avenues for structural uplift to the deprived sections.
Strategy to Tackle the Menace of Naxalism
Social Dimensions
- Aspirational District Programme deals with Left Wing Extremism (LWE) in a holistic manner for ensuring rights and entitlements of local communities and improvement in governance and management.
- Security Related Expenditure (SRE) Scheme is implemented by the Central Government to reimburses needs of security forces like ex-gratia payment to the family of civilians/security forces killed/injured in LWE violence, compensation to Left Wing Extremist cadres who surrendered in accordance with the surrender and rehabilitation policy.
- The government should initiate more dialogues between the Naxalites and the government officials. Equal participation in casting votes and contesting elections can make the conditions better.
- Providing access to the basic resources such as forests, education, sanitation, and food. There is a need to emphasis on rehabilitation and resettlement of the affected population.
Economic Dimensions
- Removing economic disparity could contribute to tackle the growth of Naxalism.
- Generation of more employment with higher wages will help the people of that region in uplifting their skills.
- There is a need of coherent national strategy to be implemented by Central Government to end Naxalism.
Developmental Dimensions
- Road Connectivity Project for LWE affected areas (RCPLWE) is implemented for further improving road connectivity in LWE affected States.
- LWE Mobile Tower Project is implemented to improve mobile connectivity in the LWE areas.
- The concern of infrastructure needs to be addressed in the Naxalite affected regions.
India has made little success tackling Naxalism, but the root causes have not been addressed yet. The central and the State Governments should continue to work together and come up with common strategy.
-
2021
Discuss how emerging technologies and globalisation contribute to money laundering. Elaborate measures to tackle the problem of money laundering both at national and international levels.
Money laundering is defined as the process that disguises illegal profits without compromising the criminals who wish to benefit from the proceeds.
Emerging technologies contribute to money laundering in following ways:
- Structuring deposits, involvement of a lot of channels popularly called as smurfs, to hide from the anti-money laundering reporting.
- Use of cryptocurrencies and alternate finance that are unregulated by governments.
- Large volume of digital transactions at online market places is used to disguise the structured chunks of layered money.
Globalisation contributes to money laundering in following ways:
- Placement of money in global financial system creates problems of coordination between multiple jurisdictions.
- Shell companies lie within the sovereign border without active business operations in the guise of legitimate transactions through fake invoices and balance sheets wherein they channel the laundered money into illegitimate businesses.
- Tax haven countries like Cayman Island, Panama etc. have structured their economies around assistance in tax evasion.
Measures at national level:
- Prevention of Money Laundering Act (PMLA), 2002 criminalises money laundering as a cognisable, non-bailable offence.
- Financial Intelligence Unit – India (FIU-IND) coordinates efforts of national and international intelligence, investigation and enforcement agencies against money laundering.
- The Black money (undisclosed foreign income and assets) and Imposition of Tax Act, 2015 deals with the menace of the black money existing in the form of undisclosed foreign income and assets.
Measures at international level:
- The Vienna Convention makes it obligatory for signatory states to criminalise the laundering of money from drug trafficking.
- The Financial Action Task Force (FATF) sets standards and promotes effective implementation of legal, regulatory and operational measures against money laundering and terror financing.
- The OECD forum has adopted convention against money laundering. It supports appropriate safeguards, access to tax administration in suspicious transaction based on information received from FIUs.
- The International Organisation of Securities Commissions (IOSCO) takes necessary steps to combat money laundering in securities and futures markets.
Money Laundering is a global menace which require global effort to curb it. Both international and national stakeholders need to come together by strengthening data sharing mechanisms and adopting a multilateral approach to effectively eliminate the problem of money laundering.
-
2021
Keeping in view of India’s internal security, analyse the impact of cross-border cyber-attacks. Also, discuss defensive measures against these sophisticated attacks.
A cyber-attack is a type of attack that targets computer systems, infrastructures, networks, or personal computer devices using various methods at hands. Depending on the context, cyberattacks can be part of cyberwarfare or cyberterrorism. A cyber-attack can be employed by sovereign states, individuals, groups, society, or organisations, and it may originate from an anonymous source.
The term ‘cross-border’ implies a movement or an activity across a border between the two countries. Impact of cross-border cyber-attacks include:
- Debilitating impact on Critical Information Infrastructure (power plants, nuclear plants, telecommunications etc.).
- It can be used as spyware to get sensitive information.
- Terrorists may use social media to plan and execute terror attacks and for virulent propaganda to incite hatred and violence.
The defensive measures undertaken to counter cross-border cyber-attacks are:
- Coordination with different agencies at the national level.
- The government needs to issue alerts and advisories regarding the latest cyber threats and countermeasures on a regular basis.
- The Information Technology Act, 2000 has deterrent provisions to deal with cyber-attacks.
- National Critical Information Infrastructure Protection Centre (NCIIPC) has been established to deal with cyber security issues.
- The National Cyber Coordination Centre (NCCC) has been set up for timely sharing of information with individual entities.
- Cyber Swachhta Kendra (Botnet Cleaning and Malware Analysis Centre) has been launched for detection of malicious programs and provide free tools to remove the same.
- The Technology Development Board and Data Security Council of India (DSCI) have jointly decided to promote cyber security start-ups in India.
The need of the hour is to produce a futuristic National Cyber-Security Policy which allocates adequate resources and addresses the concerns of the stakeholders.
-
2021
Analyse the multidimensional challenges posed by external state and non-state actors, to the internal security of India. Also discuss measures required to be taken to combat these threats.
Internal security has assumed core importance for India. As India now aspires and rises to taking the high seat in the comity of nations, the security challenges become more compounded and complex. India faces multifold threats from external states and non-state actors on the internal security front. State actors include the foreign government representative and their agencies. Non-state actors may include NGOs, multinational companies, terrorist and religious groups, hackers, etc.
Challenge posed by external state actors:
- A few of India’s bordering countries support the insurgent groups through funding, training, or coordination. For example, China is alleged to support insurgents in the North-East.
- There have been instances where state actors have been responsible for carrying out cyber warfare through hacking and other espionage.
- State actors also fund their proxies in and out of India to spread instability within the country and tarnish its stature at the global platforms.
Challenges posed by non-state actors:
- Multi-national Companies (MNCs) have the potential to threaten national security, especially in the data security and cyberspace domains, and by influencing the policies of their respective governments. It is the reason several Chinese apps were blocked in India recently.
- Non-state organisations with anarchic and fundamentalist ideologies repugnant to the secularist credentials of India are potential threats to the peaceful internal security environment of the nation.
- Propagandas are run and funded by enemy countries and other non-state actors (NGOs and civil society organisations) to destabilise India by damaging the socio-religious fabric and ensure riots.
Following measures shall be undertaken to combat the internal security challenges:
- There must be effective communication and coordination between intelligence agencies and law enforcement agencies.
- Sound cyber security measures must be in place to prevent any attempt of cyber attacks.
- Collaboration should be there between the government, media and the public to ensure quick and efficient sharing of information about suspicious activities to the law enforcement agencies.
We need to understand national security in a comprehensive sense and not in narrow military terms only. While it is imperative to guard our borders and strengthen our diplomacy, we also need to check the various non-state actors who come in hidden forms. There is a need for a national internal security doctrine to deal with various challenges.
-
2021
Analyse the complexity and intensity of terrorism, its causes, linkages and obnoxious nexus. Also suggest measures required to be taken to eradicate the menace of terrorism.
Terrorism can be defined as the calculated use of violence or the threat of violence to inculcate fear; intended to coerce or to intimidate governments or societies in the pursuit of goals that are generally political, religious, or ideological.
Causes of terrorism:
- Lack of political legitimacy and continuity, as well as a lack of integration for the political fringes, encourages ideological terrorism.
- Perceptions of deprivation and inequality, especially amongst culturally defined groups. This can lead to civil violence, of which terrorism may be a part.
- Terrorist tactics are used not out of a random desire to fire rockets at civilians but to leverage violence to gain specific concessions.
- Socio-economic explanations of terrorism suggest that various forms of deprivation drive people to terrorism, or that they are more susceptible to recruitment by organisations using terrorist tactics. Poverty, lack of education or lack of political freedom are a few examples.
- Extreme ideologies may sometime result in hatred towards other sections of society and may lead to terrorism. Examples of terrorist groups motivated by ideology include the Irish Republican Army (IRA) and the Liberation Tigers of Tamal Eelam (LTTE).
The linkages and obnoxious nexus of terrorism include:
- Terrorism and organised crime aid each other to thrive and survive. The financial proceeds of organised crime such as extortion/kidnapping are made legal through money laundering and then used to fund terrorist activities.
- Terrorist groups levy taxes on drug traffickers to provide security to criminals in their controlled area.
- Terrorist groups act as proxies of enemy governments which in turn provide them funding and shelter.
The measures undertaken to combat terrorism are:
- Adoption of a Comprehensive Convention on International Terrorism.
- Strengthening national coordination mechanisms to promote inter-agency participation and information exchange, facilitating joint monitoring, threat assessment.
- Updating national legislation to ensure that terrorist and organised crime offences are precisely defined.
- Awareness generation and deradicalization of the youth to wean them away from the clutches of their influencers.
-
2020
Discuss different types of cyber crimes and measures required to be taken to fight the menace.
Cyber crime is a criminal activity thatinvolves computersor anynetworkdevicesthattargetindividuals, companies, and governments for direct financial gain or to sabotage or disrupt operations. Cyber crime is a major threat to sectors identified under Critical Information Infrastructure (CII) that include financial systems, air traffic control and telecommunications.
Different types of Cyber crimes
- Malware, short for malicious software, refers to any kind of software that is designed to cause damage to a single computer, server, or computer network. Ransomware, Spyware, Worms, viruses, and Trojans are all varieties of malware.
- Phishing: It is the method of trying to gather personal information using deceptive e-mails and websites.
- Denial of Service attacks: A Denial-of-Service (DoS) attack is an attack meant to shut down a machine or network, making it inaccessible to its intended users. DoS attacks accomplish this by flooding the target with traffic or sending it information that triggers a crash.
- Man-in-the-middle (MitM) attacks, also known as eavesdropping attacks, occur when attackers insert themselves into a two-party transaction. Once the attackers interrupt the traffic, they can filter and steal data.
- Social engineering is an attack that relies on human interaction to trick usersinto breaking security procedures to gain sensitive information that is typically protected.
Measures to be taken
- Real-time intelligence is required for preventing and containing cyber-attacks.
- Periodical ‘Backup of Data’ is a solution to ransomware.
- Using Artificial Intelligence (AI) for predicting and accurately identifying attacks.
- Using the knowledge gained from actual attacks that have already taken place in building effective and pragmatic defense.
- Increased awareness about cyber threats for which digital literacy is required first.
- There is a need to secure the computing environment and IoT with current tools, patches, updates and bestknown methods in a timely manner.
- The need of the hour isto develop core skillsin cybersecurity, data integrity and data security fields while also setting stringent cyber security standards to protect banks and financial institutions.
One of the highest numbers of cyber threats have been detected in India, and the country ranks second in terms of targeted attacks. Banking and Telecom are the most attacked sectors, but manufacturing, healthcare, and retail have also faced a significant number of cyber-attacks. Thus, there is an urgent need to take protective measures to tackle this menace.
-
2020
For effective border area management, discuss the steps required to be taken to deny local support to militants and also suggest ways to manage favourable perception among locals.
India shares its border with seven countries, and it occupies a major strategic position in Southern Asia, therefore, it is necessary to manage the borders properly. Governments make a huge investment and provide good support for border security. Still, border management poses major challenges around the world.
Steps required to be taken
- Employment opportunities: Provide employment opportunities to the youth so that they can do away with the militancy and therefore instead of supporting the militants, they will oppose them.
- Grassroot Democracy: Conducting local body elections in re-establishing the grassroot level democracy which results into the extended support from community in development processes.
- Media Facilitation Centers: Setting up of Media Facilitation centers to reduce the trust deficit since these centers provide internet services to the reporters and freelancers.
- Intelligence Grid: Strengthening the technical intelligence grid to track any terror suspect and prevent terrorist attacks with real time data. It will also enhance human intelligence networking.
Way Forward
- Without the development process, there will be no organic end of the causes of discontent and unrest.
- Social empowerment by means of skills, education, employment opportunities, human rights, rule of law have enough potential in tackling the unfavorable perception among the locals.
- Also, controlling the misinterpretation of culture, hate speeches and ignorance will enhance the process of persuasion and cognitive change.
-
2020
What are the determinants of left-wing extremism in Eastern part of India? What strategy should the Government of India, civil administration and security forces adopt to counter the threat in the affected areas?
Left Wing Extremism (LWE) organizations are the groups that try to bring change through violent revolution. They are against democratic institutions and use violence to subvert the democratic processes at ground level.
Determinants of Left-Wing Extremism in Eastern Part of India
- India’s land reform policy: The land reform policies of India could not be successful in some parts of the nation post-independence, which led to the growth of Maoists and Naxals in India.
- Tribal issues: Tribals face exploitation and harassment from government and corporate bodies to extract resources since eastern region is rich in natural resources including forests, minerals and mines. Also, issues of trafficking of women and girls are mostly seen among tribal groups.
- Development deficit and forced displacement: In this region, people are solely dependent on the primary sector since the region has significant natural resources. Exploitation of the natural resources for economic progress has led to the forceful displacement of tribal which results into the alienation of tribal community.
- Government deficit: Government is unable to provide sufficient education facilities, basic healthcare facilities, employment, etc. in eastern part of India. Also, there are issues related to law and order and grievance redressal. Poor implementation of special laws and mismanagement of schemes like PDS.
Strategies to be taken to counter such menace:
- Innovative measures are required to be employed in preventing IED (Improvised Explosive Device) related incidents which have caused significant casualties in recent years.
- States play a vital role in maintaining law and order. So, emphasis should be laid on the capacity-building and modernization of the local police forces. Local forces can efficiently and effectively neutralize the LWE organizations.
- States should rationalize their surrender policy to bring innocent individuals caught in the trap of LWE in the mainstream.
- Rehabilitation plans for surrendered Naxalites.
- National Policy and Action plan to address LWE.
For the holistic last-mile development of “New India”, it is necessary to get rid of the menace of such radicalized groups and the synergized efforts of the Centre and the States are crucial in achieving the same.
-
2020
Analyze internal security threats and transborder crimes along Myanmar, Bangladesh and Pakistan borders including Line of Control (LoC). Also discuss the role played by various security forces in this regard.
India has a large and complex border covering around 15106.7 km, which it shares with Bangladesh, China, Pakistan, Nepal, Myanmar, Bhutan as well as a small portion with Afghanistan.
Challenges in the effective border management particularly to Myanmar, Bangladesh and Pakistan:
- India-Myanmar Border: The northeastern states of Arunachal Pradesh, Nagaland, Manipur, and Mizoram share the border with Myanmar. Some of the insurgent groups like the National Socialist Council of Nagaland (NSCN) and the United Liberation Front of Asom (ULFA) operate from Myanmar, which threatens the security of India as well as Myanmar. Porous nature of the border provides safe route to human traffickers, illegal arms dealers, drug smugglers etc.
- India-Bangladesh Border: The Indo-Bangladesh Border (4,096 km) passes through West Bengal, Assam, Meghalaya, Tripura, and Mizoram. The entire stretch consists of plains, riverine belts, hills and forests which make illegal migration easy. Illegal migration across this border poses serious security threats and acts as a fertile ground for organizations like the Inter-Services Intelligence of Pakistan to penetrate and expand their activities. Also, the poor law and order situation at the border has led to smuggling of arms and drugs. Supply of arms help in sustaining any conflict.
- India-Pakistan Border: Indo-Pakistan Border (3,323 km) runs along the states of Gujarat, Rajasthan, Punjab and Jammu & Kashmir. Direct accessibility of the borders and some technological developments enabling quick passage of information and transfer of funds has changed the focus and tenor of border security. Cross-border terrorism from Pakistan has exacerbated due to non-recognition of boundaries by its terrorist groups and their success in acquiring legitimacy due to religious or ethnic identity.
Role played by various security forces in this regard
- Assam Rifles: This force significantly contributed to opening the region to administration and commerce and over time they came to be known as the right arm of the civil and left arm of the military.
- Border Security Force: The BSF has air wing, marine wing, an artillery regiment, and commando units. It currently stands as the world’s largest border guarding force. BSF has been termed as the First Line of Defence of Indian Territories. It is India’s primary border guarding organization on its border with Pakistan and Bangladesh.
- Sashastra Seema Bal: The sole objective of this force is achieving ‘total security preparedness’ in the remote border areas for performing a ‘stay-behind’ role in the event of a war. SSB is now spread along the International Border across Uttarakhand, UP, Bihar, West Bengal, Sikkim, Assam, and Arunachal Pradesh.
India should endeavor to meaningfully engage with Myanmar, Bangladesh and Pakistan and solicit their cooperation in resolving all outstanding issues and better manage their mutual border.
-
2019
The banning of ‘Jamaat-e-islaami’ in Jammu and Kashmir brought into focus the role of over-ground workers (OGWs) in assisting terrorist organizations. Examine the role played by OGWs in assisting terrorist organizations in insurgency affected areas. Discuss measures to neutralize the influence of OGWs.
Terrorism instils an innate sense of fear in the citizen and dilutes the perceived control of the state over law and order. This state of lawlessness creates conditions which help the terrorist group achieve its political aims. Overground workers(OGWs) provide a support system to terrorist groups and networks in carrying out their activities in insurgency affected areas.
The role played by OGWs
- Food and Logistics support: OGWs assist terror networks to meet their basic needs.
- Propaganda and radical narrative: This provide the ideological background to the terror outfits.
- Finding new recruits: Pool of Disgruntled youth provide a fertile ground for OGWs to propagate radicalisation and hire new recruits.
- Coordination with other stakeholders: OGWs coordinate with secessionist leaders, and Organised crime Networks to meet their political objectives.
- Conduit for Illegal Money: This is done through illegal trade, counterfeit currency, Tax evasion and Hawala transactions. These funds are also used to instigate anti-state protest like stone-pelting.
- Assist in the planning and execution of terror plans: They provide operational planning, intelligence information, safety routes, maps and other inputs that are needed for terror operations.
Measures to neutralize the influence of OGWs
- Address the root cause of alienation among affected communities: This is done by addressing genuine concerns and through awareness campaigns that dispel false propaganda.
- Rehabilitating orphans and women: This would fulfil the state’s duty to ensure Social welfare. Also, It would counter the influence of OGWs to find new recruits.
- Intelligence Infrastructure: To keep track of radicalisation attempts by OGWs and recruitment agents in order to stop this process at its inception.
- Human and Electronic Surveillance: This is used to tap into existing networks to pre-empt terror attempts.
- International cooperation: To facilitates follow up on suspects and terror networks.
- Fast track courts: Laws like Public Safety acts for the speedy conviction of terrorists and OGWs through fast track special courts.
However, Misuse of the legal provision in the random booking of youth on mere suspicion should be avoided. The best defence against terrorism is to ensure that the people do not have the incentive to pick up arms against the country by providing them equitable political, social and economic opportunities.
-
2019
What is CyberDome Project? Explain how it can be useful in controlling internet crimes in India.
CyberDome project is a technological research and development centre of Kerala Police Department, conceived as a cyber centre of excellence in cyber security, as well as technology augmentation for effective policing.
It envisages as a high tech public-private partnership centre of collaboration for different stakeholders in the domain of cyber security and handling of cyber crimes in a proactive manner.
India has witnessed a 457% rise in cybercrime incidents under the Information Technology (IT) Act, 2000 from the year 2011 to 2016.
CyberDome project can be useful in controlling these internet crimes in India
- The project can help in preventing cyber crimes through development of a cyber threat resilient ecosystem in the country to defend against the growing threat of cyber attacks. To effectively tackle cybercrime, the Government has collaborated with private sector and academia to conform rapidly changing technology world.
- The Cyberdome will act as an online police patrol. Through its Anti-Cyber Terror Cell and a cybersecurity training unit, its officers will generate intelligence on various cyber threats in near real time and track fugitives online by monitoring their online activities, including social networking sites.
- It will create a digital repository of stolen and lost vehicles and travel documents, track online payments to prevent money laundering and channelling of funds to dubious organisations and issue cyber security advisories.
- Cyberdome would have centres for social media awareness, protection of children on the Internet, Internet monitoring and ICT (Information and Communication Technology) in service delivery.
- Cyberdome in collaboration with the RBI, Banks, payment gateways and other wallet groups can tackle financial fraud.
- Through its ransomware school, CyberDome can understand, analyse and mitigate ransomware infections, create standard operating procedures to deal with ransomware, creating awareness among the public as well as government departments about ransomware and its precautionary steps.
- The Cyberdome is expected to enable sleuths to obtain vital leads in cases of cyber-related offences using advancements in the field of information technology.
- Of late, Cyberdome has used social engineering as the lynchpin of its policing strategy to snoop on radical groups that use the net for extremist activities.
- Cyberdome has made successful propaganda war against online games such as Blue Whale.
- Of late, Cyberdome has launched a covert cyber-surveillance and infiltration programme to crack down on child pornography. Thus, Cyberdome project has great potential to control internet crimes and must be replicated at the national level.
-
2019
Indian government has recently strengthed the anti-terrorism laws by amending the unlawful activities (Prevention) Act, (UAPA), 1967 and the NIA Act. Analyze the changes in the context of prevailing security environment while discussing scope and reasons for opposing the UAPA by human rights organisations.
The Union Government by amending NIA Act and UAPA Act seeks to provide more powers to India’s anti-terror agency and expand the scope of India’s anti-terror law, thereby providing a big push to India’s internal security machinery.
Under the UAPA Act, the Central Government can designate an organisation as a terrorist organisation if it commits or participates in acts of terrorism; promotes terrorism; or is otherwise involved in terrorism. Currently, only an organisation can be declared a terrorist. The amendment allows government to designate individuals suspected to have terror links as 'terrorists'.
Likewise, the amendment to NIA Act widens the powers of the National Investigation Agency (NIA) to investigate crimes related to human trafficking, counterfeit currency, dealing in prohibited arms, and cyber-terrorism. These were earlier under State police. NIA can also investigate a crime irrespective of its place of occurrence.
These amendments are in pursuance of the government’s zero-tolerance policy against terrorism. These hold significance in the context of the prevailing security environment.
- Terrorism emanating from Pakistan has been a consistent challenge whereby terrorist organisations have been devising new methods to threaten the stability of the region.
- This often included formation of new terrorist outfit by the individuals if their previous organisation was banned. This issue emerged during India’s efforts to designate Masood Azhar as terrorist when some foreign diplomats questioned India’s domestic law which didn’t provide for individual’s designation. Now, declaring an individual as a terrorist will help the government to deal with such situations.
- Besides, there is growing menace of terror financing and organised crimes like human trafficking, cyber terrorism etc. An empowered NIA is a good step in this direction
However, human rights organisations allege that these amendments violate the basic human rights and seek to create a police state.
- The UAPA does not clearly define a ‘terrorist act’.
- The presumption of innocence is considered a universal human rights principle but the UAPA creates a presumption of guilt for terrorist offences based on the seized evidence.
- Moreover, there is no set procedure for designation as a terrorist. By excluding judiciary and empowering the executive to designate, it dilutes the difference between a terrorist and a terror accused.
- Similarly, the term 'affecting the interest of India' in NIA act is undefined and the civil society fears that it can be used to curb freedom of speech and expression.
Thus, though the changes are required to meet the prevailing security environment, the policy framework dealing with terrorism must incorporate the state duty to protect against human rights abuses and greater access of victims to remedies. Apart from dealing with terrorism, emphasis should be on to improve the functioing of the police force and to make India’s judicial mechanism faster.
-
2019
Cross-border movement of insurgents is only one of the several security challenges facing the policing of the border in North-East India. Examine the various challenges currently emanating across the India-Myanmar border. Also, discuss the steps to counter the challenges. (250 words)
India and Myanmar share a long 1,643 km geographical land border and maritime boundary in the Bay of Bengal, which act as India’s gateway to South-East Asia.
India-Myanmar border is highly porous, poorly guarded and located along a remote, underdeveloped, insurgency-prone region and proximate to opium producing area.
Various challenges across the India-Myanmar border
- Cross-Border Terrorism: Indo-Myanmar border area have become a safe haven for dozens of insurgent groups. These insurgent groups performs offensive action in India and brings instability to the area by promoting separatist tendencies and take an easy hide in Myanmar.
- These groups also take advantage of loopholes in free movement regime across border to supply arms and drugs in India.
- Connectivity: Several connectivity projects like Kaladan Multi-Modal project and IMT Trilateral Highway project are underway, but the ground level progress is quite unfortunate.
- Free Movement Regime: It permits tribals to travel 16 km across the borders without any visa restrictions and allowed them to carry heavy loads. This loophole is well utilized by insurgents for trafficking of arms and drugs and to find safe havens in Myanmar.
- Boundary Agreement 1967: Though the agreement has delineated the borders between the two countries but not much has been crystallised on ground level.
- Tribal Linkages: The Indo-Myanmar border is densely populated with tribals, and these tribal communities have strong social-cultural linkages across borders and they refuse to accept the artificial border lines.
- Security Forces: Assam Rifles had a responsibility of guarding the Indo-Myanmar border, but most of it battalions are engaged in counter-insurgency operations. Therefore, it functions like counter-insurgency force rather than border-guarding force.
- Infrastructural Facility at Border Check-Points: The infrastructure facilities at border check-points is not sufficient to meet the required challenge. Moreh-Zokhawater point has been declared as Integrated Check-Point (ICP) but nothing much have materialised on the ground.
- Difficult Terrain Across Border: The geographical terrain around border areas is highly inaccessible, so it becomes quite difficult to develop communication and connectivity.
- Trafficking: Proximity to ‘golden triangle’ has made Indo-Myanmar border highly vulnerable to drug trafficking and the border has become a gateway for trafficking of women and small children to South Asian Nations.
- Rohingya Issue: Influx of marginalised muslim minority rohingya community has raised a serious sociocultural confrontations in the areas due to increased burden on local resources.
Steps to Counter the Challenges
The vulnerability of the India-Myanmar border is posing a serious challenge to the internal security of the country. The Government of India should pay immediate attention to effectively manage this border.
- It should strengthen the security of the border by either giving the Assam Rifles the single mandate of guarding the border or deploying another border guarding force such as the Border Security Force (BSF).
- It should initiate a revision of the FMR and reduce the permitted distance of unrestricted travel.
- The construction of the ICP along with other infrastructure should be expedited.
- The Comprehensive Integrated Border Management System (CIBMS) which is touted as a robust and integrated system, is capable of addressing the gaps in the present system of border security by seamlessly integrating human resources, weapons, and high-tech surveillance equipment, should be proactively deployed.
- Sustained community interaction programmes so that the border tribal communities can be sensitised to participate in the nation building on both sides of the border.
India should endeavour to meaningfully engage with Myanmar and solicit its cooperation in resolving all outstanding issues and better manage their mutual border.
- Cross-Border Terrorism: Indo-Myanmar border area have become a safe haven for dozens of insurgent groups. These insurgent groups performs offensive action in India and brings instability to the area by promoting separatist tendencies and take an easy hide in Myanmar.
-
2018
Left Wing Extremism (LWE) is showing a downward trend, but still affects many parts of the country. Briefly explain the Government of India’s approach to counter the challenges posed by LWE. (2018)
The Government’s approach is to deal with Left Wing Extremism in a holistic manner, in the areas of security, development, improvement in governance and public perception management. Recently, Government has come out with operational strategy ‘SAMADHAN’ to fight Left Wing Extremism in the country.
Government’s Approach:
- Governance and Development: The foremost focus of Government is to strengthen the connectivity in these areas so as to improve its engagement with the rest of the country. Infrastructural enhancements like road, railways and airport construction, instalment of mobile towers are taking place. For example- National Policy and Action Plan.
- Smart Leadership and better coordination with the State governments is being encouraged by the Government to expand its reach in the LWE affected areas.
- An aggressive strategy is being followed to modernise and strengthen the capacity of armed forces.
- Special emphasis is being laid on the implementation of Forest Rights Act and ensuring entitlement of local communities over Minor Forest Produce.
- No Access to Financing: To stop the maintenance and sustained survival of Left Wing Extremism, the Government is attempting to block Left Wing Extremist outfits’ access to financing.
- Rehabilitation and Surrender: Surrender-cum-Rehabilitation Scheme is being implemented to ensure militants’ rehabilitation and return to the mainstream.
- Public Perception Management: To counter the ideological effect of Left Wing Extremism on people, gaps between Security Forces and local people are being bridged through close interactions, Tribal Youth Exchange programmes, radio jingles, documentaries, pamphlets etc.
-
2018
Data security has assumed significant importance in the digitized world due to rising cyber crimes. The Justice B.N. Srikrishna Committee Report addresses issues related to data security. What, in your view, are the strengths and weaknesses of the Report relating to protection of personal data in cyber space? (2018)
The threat from cyber crime is multi-dimensional, targeting citizens, businesses, and governments at a rapidly growing rate. The Committee under the chairmanship of Justice B. N. Srikrishna was constituted to examine issues related to data protection, recommend methods to address them, and draft a data protection law. The objective was to ensure growth of the digital economy while keeping personal data of citizens secure and protected. The report inter alia presented a draft Personal Data Protection Act.
Some of the Important Strengths and Weakness of the Report:
- The Committee noted that consent is treated as one of the grounds for processing personal data.
- One in three internet users across the world is children under the age of 18. A data protection law must sufficiently protect their interests, while considering their vulnerability, and exposure to risks online.
- It discussed the principle where personal data must be collected for a specified purpose only.
- One of the principles of data protection is that a person whose data is being processed should be able to influence the processing. This includes the right to confirm, access, and rectify the data.
Weakness
- Who owns the data of the individuals is a question not answered by the Committee as against the TRAI recommendation that ownership of data must rest with the individual.
- Globally, the right to be forgotten refers to the right to erase data. Srikrishna panel, says “...data principal shall have the right to restrict or prevent continuing disclosure of personal data by a data fiduciary related to the data principal where such disclosure has served the purpose for which it was made or is no longer necessary; was made on the basis of consent... and such consent has since been withdrawn; was made contrary to the provisions of this Act or any other law made by Parliament or any State Legislature.”
- On data breach, the Committee recommended that such a breach must first be reported to the Authority. This suggestion has been criticized and it is argued that it should be first reported to the subject of the breach instead.
-
2018
India’s proximity to the two of the world’s biggest illicit opium growing states has enhanced her internal security concerns. Explain the linkages between drug trafficking and other illicit activities such as gunrunning, money laundering and human trafficking. What counter measures should be taken to prevent the same? (2018)
Geographically, India is placed between the two largest opium growing areas in the world. To the west is the Golden Crescent (Afghanistan) and to the east is the Golden Triangle (Myanmar). This makes India vulnerable to drug trafficking through its borders and other illicit activities, and has enhanced her internal security concerns.
There exist linkages between drug trafficking and other illicit activities such as gunrunning, money laundering and human trafficking, which are as follows:
- An increasing interoperability has been witnessed between drug cartels and other criminal groups. In Afghanistan around 85% of the opium growing area falls under Taliban. Taliban uses the funds from drug trade in many different ways like weapons smuggling, human trafficking, and proliferation of terrorism etc.
- Drug trafficking groups also get attracted to human trafficking activities as there is some overlap between the routes used and there are advantages to be gained by sharing established logistical infrastructure, which includes transportation and storage facilities.
- Similarly, gunrunning and money laundering require logistics supports which are shared by these organizations. At times these activities seem to sustain each other such as smuggling drugs by hiding it in human body parts. The revenue generated from drug trade is laundered to create assets such as casinos, bars, hotels etc. which again became breeding grounds for other crimes. Nexus between drug lords and armed groups gives rise to thriving weapons business.
Following counter-measures can be opted against these crimes:
- As these crimes are trans-national in character, countering them requires cooperation among all countries.
- Making the border management more robust and plugging the gaps by bringing in force the recommendations of Madhukar Gupta Committee on border protection. The committee has given broad recommendations on the issues of Threats and Border Protection, assessment of force level, deployment on the border, infrastructure and technology issues for protection of border and administrative issues
- Making the police and the concerned authorities acquainted to dark web and other modes of operation.
- Sensitizing the public against negative fallouts of drugs and starting rehabilitation programmes.
This drug problem is a serious menace giving impetus to various other crimes, so strong political will and hard measures if required should be opted to tackle this challenge. Technical solutions are also necessary to augment and complement the traditional methods of border guarding. Working on both the front can probably address the existing problems of internal security.
-
2017
Discuss the potential threats of Cyber attack and the security framework to prevent it. (2017)
The benefits of cyberspace to citizens, businesses and governments are considerable and
far reaching . While technologies are overwhelmingly created for positive use, they can be exploited as well. Crimes in cyberspace cost the global economy around $450 billion a year.Potential threat
Cyber attack is a particularly major threat to sectors identified under Critical Information Infrastructure (CII) that include financial systems, air traffic control
and telecommunications.First, all the sectors identified as CII are dependent on connectivity.
Debilitating attack on any one system can cause a cascading effect, disrupting the functioning of other systems.Second, CII is highly dependent on industrial control systems, which depend on digital instructions. Any malicious takeover of these systems will not only disrupt but also seize functioning of CII.
Third, many CII, such as air traffic control, is dependent on navigational data, which is especially vulnerable to spoofing. If the integrity of this data cannot be ensured, the input of false data can have disastrous consequences.
Security Framework
The Indian government has also been aggressively addressing the rising prevalence of cyber threats. National Cyber Security Policy 2013 has been framed to create a secure cyber ecosystem, ensure compliance with global security systems and strengthen the regulatory framework. The union budget for 2017 included the formation of Computer Emergency Response Team (CERT) for the financial sector.
The government has also sought data security protocol details from several
smart phone manufacturers insisting that mobile manufacturing units be security-compliant. The Technology Development Board and Data Security Council of India (DSCI) have jointly decided to promotecyber security startups in India.NASSCOM and DSCI
Cyber security Task Force have also launched a roadmap to develop thecyber security ecosystem to $35 USD billion by 2025. -
2017
The North-Eastern region of India has been infested with insurgency for a very long time. Analyze the major reasons for the survival of armed insurgency in this region. (2017)
Due to its distinct socio-cultural background and particular historical evolution, the North-East region of India holds several fault lines around which many insurgent groups have been thriving for a very long time. The major reasons behind the evolution and survival of armed insurgency in this region are-
- This region has been one of the most neglected regions in terms of developments and is the main cause behind the resentment of the people living in this area. The insurgent groups take advantage of resentment of people and get support base.
- Alienation of population from
mainstream political process, where the insurgent groupcontinue to boycott the dialogue and electoral process. (Ex – NSCN-Khaplang group) - Hilly terrain, dense forest
and porous borders give strategic advantages for the insurgent Guerilla groups and at the sametime it createsbig hurdle for thecounter insurgency operations. - Racial clashes are very common here due to
diverse racial profile of the region. In a fracturedsociety the insurgent groups penetrate easily. - Active and covert foreign support to these insurgent groups, through training, logistic and moral support has also been a big hurdle to eradicate these groups.
The twin approach of development and
counter insurgency operations coupled with honest political dialogue process may provide the best answer to the long infested insurgency in the North-East. - This region has been one of the most neglected regions in terms of developments and is the main cause behind the resentment of the people living in this area. The insurgent groups take advantage of resentment of people and get support base.
-
2017
Mob violence is emerging as a serious law and order problem in India. By giving suitable examples, analyze the causes and consequences of such violence. (2017)
Over the past few years, there have been increasing incidents of loss of life and property due to mob violence – whether it be in Jharkhand over
rumours of child kidnapping, in UP and Rajasthan by cow vigilantes, in Kashmir by violent crowds or over reservation by Jats in Haryana. Mob violence can be seen as a reflection of the displacement of responsibility by the state, which blames people for taking law into their own hands, and by citizens, who justify their actions on state inaction.Causes for Increasing Mob Violence
- Motivated
rumours spread through social media which acts as an anonymous force multiplier. Climate of impunity - Mob violence and vigilantism happens because criminals expect to get away with it. State deterrence is not perceived to be credible, especially when policemen are rendered as mereby-standers at the scene of violence.- General erosion of law and order situation - inadequate response to societal disorder, and its inability to aggressively prosecute those involved in vigilante killings further encourages mob violence.
- Silence by society – People who are mute witnesses to such incidents, are just as responsible when they stay away from expressing their disapproval to such incidents for the fear of being caught in the cross-fire.
Consequences of increasing Mob Violence
- There is
deficit of justice when incidents of lynching across states happen, without those responsible being held accountable. - There is
perversion of democracy, which confers upon the people an absolute monopoly on violence. - Mob Violence threatens the very existence of dignified and meaningful existence in India enshrined in one of the Fundamental rights i.e. “Right to Life” (Art 21).
Therefore, there is
need for comprehensive police reforms and efficient criminal justice delivery system which acts as a deterrence to people from resorting to mob violence in the name of justice. - Motivated
-
2017
The scourge of terrorism is a grave challenge to national security. What solutions do you suggest to curb this growing menace? What are the major sources of terrorist funding? (2017)
India has been hit by terrorism
since a long time, like, 1993 Bombay blasts, attack on Parliament in 2011, the 26/11 Mumbai attacks, Pathankot attacks etc. In view of such attacks it becomes imperative for India to check this rising menace, for which the following steps can be taken:- Ensure
co-ordination among the intelligence and security agencies to check infiltration of terror activity. - Empowering and engaging with civil society and local communities can help in countering radicalization and to stop the spread of violent extremism.
- Given the important role of educational establishments in promoting the values of non-violence, peaceful coexistence and tolerance, education must feature prominently in
counter radicalization programs. - Several initiatives that promote
alliance of civilizations and intercultural dialogue must be promoted to counter terrorism. For instance, the Rashtriya Ekta Diwas celebrated on 31st October promotes unity in India. - Enhancing security presence along the international boundaries and seal the porous borders.
- Undertaking policies to tackle economic and social inequalities will help in deterring disgruntled youth from being lured towards terrorism.
- Terrorist organizations have successfully taken advantage of the great benefits of the Internet. Hence, countering radicalization on digital media must be given priority. Governments should intervene in this matter through monitoring and counter-propaganda programs
- Incorporating ‘SAMADHAN’ in security operations in LWE affected areas and at
same time focusing on development projects in Red corridor districts.
Sources of funding
- NGO, charities
and donations are an important sourcing of funds for terrorism. These funds are mostly claimed through religious appeal, coercionand fears of victimization. - Counterfeiting of Indian currency not only funds
terrorism, but, more importantly, it is used as a tool by neighboring states to destabilize the Indian economy. - Drug financing
are alsoa major sources of terrorism financing in India. Biggest source of internal funding for terrorist groups in India remains extortion. This is especially relevant for groups in the North-East and the Maoist-affected areas.
- Ensure
-
2016
The terms ‘Hot Pursuit’ and ‘Surgical Strikes’ are often used in connection with armed action against terrorist attacks. Discuss the strategic impact of such actions. (2016)
With the Indian forces carrying out “surgical strikes” across the Line of Control, India seems to have abandoned the self-proclaimed policy of “strategic restraint” adopted in the face of earlier provocations by terrorists believed to be backed by Pakistan. This may not be the first time India has undertaken quick cross-LoC operations, but it has never before chosen to share information so publicly.
Strategic impact of this action can be following.
- This surgical strike indicates that India’s technical capabilities (Command, Control, Communications, Computers, Intelligence, Surveillance and Reconnaissance — C4ISR) have improved a great deal.
- The terms “surgical strike” and “pre-emptive strike” used by India were intended to make it clear to the enemy that there will be repercussions and crossing the border does not guarantee immunity
- The strikes proved to be an important element for maintaining the morale of the people of India and the armed forces.
- The strike reinforced the credibility of the government and displayed its resolve, even as justified restraint and maturity was on display. This act would also counter India’s image of being a soft state.
- Russia has also backed India, saying Pakistan should take effective steps in order to stop activities of terrorist groups in its territory. India seems to have played its cards well by seeking international and regional isolation of Pakistan before striking infiltrator targets across the LOC.
There are also several negative impacts of these types of acts as it may escalate the conflict especially in case of Pakistan, Security forces can be trapped in enemy territory. It could be a cause of international censure for violating other country’s border.
-
2016
‘Terrorism is emerging as a competitive industry over the last few decades.” Analyse the above statement. (2016)
In recent years, with the emergence of new terrorist organizations like ISIS, Boko Haram etc. terrorism has become a competitive industry. Like mafia organizations, where one-upmanship is often based on who has the most guns, money or local power, terrorist groups too have a pecking order.
The current competitive market in terrorism means that groups are trying to distinguish each other through the practice of more memorable violence (like the Charlie Hebdo attacks or the Peshawar attacks in December 2014). They need to do so because this is the only way in which they can be heard, become popular enough to attract recruits and distinguish themselves from other similar groups. In order to do so the terrorist groups are trying to out-do each other in the intensity and scope of violence and bloodshed they can cause so that more people can identify with them and join them. For example- while some years back, Al-Qaeda was the most dreaded terrorist group of the world, this position has now been overtaken by ISIS. One of the reasons for this can be because ISIS encourages lone-wolf attacks which are easier for its followers to carry out without actually travelling to join the group to fight in combat.
Various terrorist organizations are also in competition with each other to get control of various natural resources such as oil reserves in Middle East countries, cultivation of Opium, arms dealing etc.
Competition over establishing their ideologies all around the world has also instigated terrorist organization for example multiple groups are fighting with each other in Syria. So in recent time terrorism has become a competitive industry that has spread its influence all over the world.
-
2016
Border management is a complex task due to difficult terrain and hostile relations with some countries. Elucidate the challenges and strategies for effective border management. (2016)
India has a very large and complex border covering around 15106.7km, which it shares with Bangladesh, China, Pakistan, Nepal, Myanmar, Bhutan as well as small portion with Afghanistan. Challenges in the effective border management particular to some neighbours are:
- Varied Terrain: India-China Border as comprising of difficult Himalayan terrain that is reason for difficulty in border management.
- Climatic Condition: Due to Himalayan polar condition, it is tough to guard border due to adverse climatic conditions. Ex: China, Pakistan
- Bitter relations with some of the neighbouring countries. Ex: Pakistan
- Porous nature of border with some countries that provides safe route to human traffickers, illegal arms dealers, drug smugglers etc. Ex: Myanmar
Owing to such peculiarities, having infrastructure and technology does not alone suffice for effective border management. Following strategies can be adopted for effective border management.
- Co-ordination among various agencies such as customs, immigration, armed forces, border security and intelligence agencies is required that will strengthen the border guarding and management.
- Smart border management to identify and implement controls which aim to improve border security by enabling effective communication and coordination.
- Use of Drone, Night vision cameras, sensors to check the illegal migration, terrorist movement can help in effective border management.
- Border fencing along the border such as with Bangladesh, Myanmar, Nepal can help in better border management.
- Coordination among neighbouring countries would also strengthen the measures taken for border management.
-
2016
Use of internet and social media by non-state actors for subversive activities is a major security concern. How have these been misused in the recent past? Suggest effective guidelines to curb the above threat. (2016)
The use of internet and social media has become a powerful tool in the hand of non-state actors such as terrorist organizations.
Use of Internet, by terrorist organization such as ISIS in recruiting youth all around the world has become a reality. Cyber warfare is gaining importance due to increasing density of internet. The Stuxnet virus affected half of the world targeting Iran nuclear facilities.
Cyber espionage is also a great threat that exposes the vulnerability of any organization, or country. The recent theft of data of lakhs of ATMs cards in India is recent example of misuse of internet by non-state actors.
Social media is also been used by the like-minded individuals as a tool for radicalization. Muzaffarnagar riots in Uttar Pradesh got intensified because of misuse of social media by non-state actors.
In these circumstances effective strategies should be adopted to curb the threat posed by internet and social media. Following are some of the guidelines that can be very useful.
- India recently appointed first Chief Information Security Officer (CISO). It will help India in developing the vision and policy to fight cyber crime and manage cyber security more effectively.
- Creation of National Cyber Security Agency (NCSA) would improve India’s resilience and defense system.
- Monitoring of content on internet by intelligence agencies such as Intelligence Bureau, RAW can prevent any attempt to radicalize youths.
- National Cyber Security Policy 2013 aims at protection of information infrastructure in cyber space, reduce vulnerabilities. A National and sectoral 24×7 mechanism has been envisaged to deal with cyber threats through National Critical Information Infrastructure Protection Centre (NCIIPC)
- Computer Emergency Response Team (CERT-In) has been designated to act as Nodal agency for coordination of crisis management efforts.